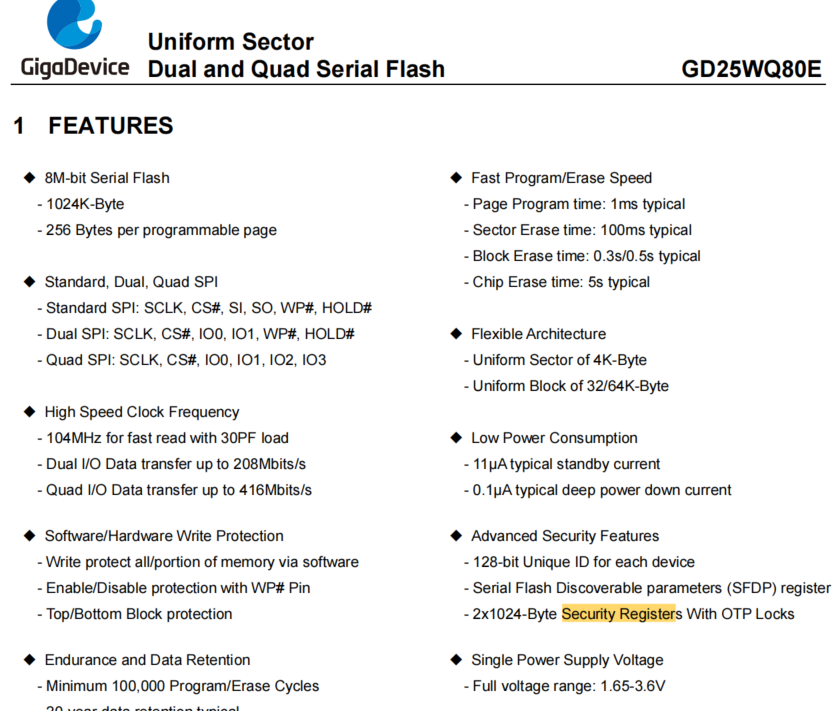
|
(1) Flash中有2x1024Byte的加密数据区域。 可以通过LB位锁定。 (2)分成4个Page。 (3)以下未例操作第1个Page 数据读写 /// #define PWR_CAL_DATA_LEN (64) //校准数据长度 #define USER_FLAG (0xAA55) //标志 #define CAL_VERSION (0x0001) //版本 #define SEC_ADDRESS_Offset (0x00) //校准数据偏移 typedef struct { uint16_t user_flag; //AA55-标志 uint16_t cal_version;//0001-版本 uint16_t power_data[PWR_CAL_DATA_LEN];//64个数据 uint16_t checksum; // 字节相加 } user_cal_data_t; user_cal_data_t user_cal_read; //#define drv_sfs_read_sec(addr, data, length) //#define drv_sfs_erase_sec(addr) //#define drv_sfs_write_sec(addr, data, length) //--------------------------------------------- void sf_security_area_test(void) { user_cal_data_t user_cal_test; uint16_t result = false; uint16_t cal_chksum = 0; // for (uint16_t i = 0; i < PWR_CAL_DATA_LEN; i++) { user_cal_test.power_data[i] = 0xa0 + i; } user_cal_test.user_flag = USER_FLAG; user_cal_test.cal_version = CAL_VERSION; user_cal_test.checksum = 0; for (int i = 0; i < sizeof(user_cal_data_t) -2; i++) { user_cal_test.checksum += ((uint8_t *)&user_cal_test)[i]; } // drv_sfs_read_sec(SEC_ADDRESS_Offset, &user_cal_read, sizeof(user_cal_data_t)); OM_LOG_DEBUG_ARRAY_EX("\n1-sf_security read", &user_cal_read, sizeof(user_cal_data_t)); if (user_cal_read.user_flag == USER_FLAG) { log_info("Flag is OK!"); cal_chksum = 0; for (int i = 0; i < sizeof(user_cal_data_t) -2; i++) { cal_chksum += ((uint8_t *)&user_cal_read)[i]; } if (cal_chksum == user_cal_read.checksum) { log_info("Checksum =0x%xis OK!", cal_chksum); result = true; } else { log_info("Checksum is ERROR!"); } } // //uint8_t readByte[262]; if (result == false) { log_info("\nread cal data ERROR!!!"); log_info("\nerase & Write user_cal_test to security area!"); drv_sfs_erase_sec(SEC_ADDRESS_Offset); // drv_sfs_read_sec(SEC_ADDRESS_Offset, &user_cal_read, sizeof(user_cal_data_t)); OM_LOG_DEBUG_ARRAY_EX("\n2-erased read", &user_cal_read, sizeof(user_cal_data_t)); drv_sfs_write_sec(SEC_ADDRESS_Offset, &user_cal_test, sizeof(user_cal_data_t)); OM_LOG_DEBUG_ARRAY_EX("\n3-sf_security write", &user_cal_test, sizeof(user_cal_data_t)); // drv_sfs_read_sec(SEC_ADDRESS_Offset, readByte, sizeof(user_cal_data_t)); // OM_LOG_DEBUG_ARRAY_EX("\n4-erased read", readByte, sizeof(user_cal_data_t)); } else { log_info("\nread cal data OK!"); } } 测试Log -------------------------------- 1-sf_security read: 55 AA 01 00 A0 00 A1 00 A2 00 A3 00 A4 00 A5 00 A6 00 A7 00 A8 00 A9 00 AA 00 AB 00 AC 00 AD 00 AE 00 AF 00 B0 00 B1 00 B2 00 B3 00 B4 00 B5 00 B6 00 B7 00 B8 00 B9 00 BA 00 BB 00 BC 00 BD 00 BE 00 BF 00 C0 00 C1 00 C2 00 C3 00 C4 00 C5 00 C6 00 C7 00 C8 00 C9 00 CA 00 CB 00 CC 00 CD 00 CE 00 CF 00 D0 00 D1 00 D2 00 D3 00 D4 00 D5 00 D6 00 D7 00 D8 00 D9 00 DA 00 DB 00 DC 00 DD 00 DE 00 DF 00 E0 30 [134bytes] [inf]sf_security_area_test|254 : Flag is OK! [inf]sf_security_area_test|262 : Checksum =0x30e0is OK! [inf]sf_security_area_test|287 : read cal data OK! ---------------------------------- |
 sf_security_reg_access-202409194072.c
sf_security_reg_access-202409194072.c